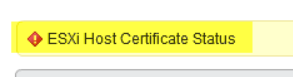
All hosts in vCenter server are showing Red Alert and notification is “ESXi Host Certificate Status”
This issue is related to certificate being used for vSphere environment. To reach to a conclude of this problem, we have to look into Self-Signed VMCA root certificate.
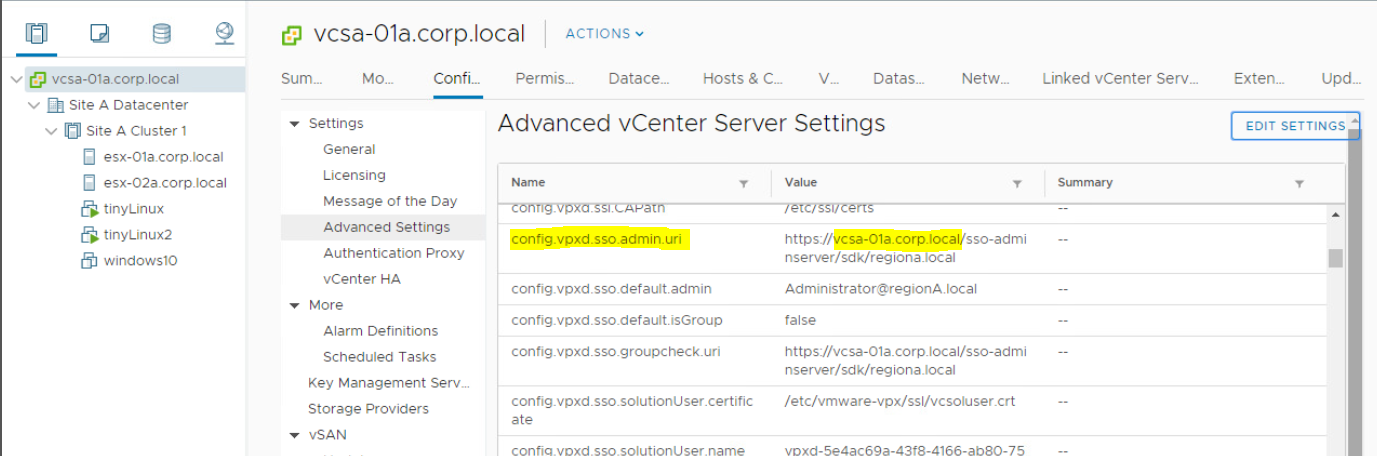
Please note that Certificates are managed by PSC server. If you are using external PSC, then you have to login to PSC server. If PSC and vCenter is running on same server, then you will use same server to login. Follow below steps to find PSC server if you don’t know.
· Select vCenter Server Name > Configure > Advanced Settings
· In right side, you will get Search option. Type SSO in search option.
· Check the value of config.vpxd.sso.admin.uri
· This is your PSC Server.
· Login to PSC server using Web Client. (https://vi-psc-01/psc)
· Under Certificates tab, Click on Certificate Store > At right panel under, drop down Store > Select TRUSTED_ROOTS. All existing certificates will be in this list.
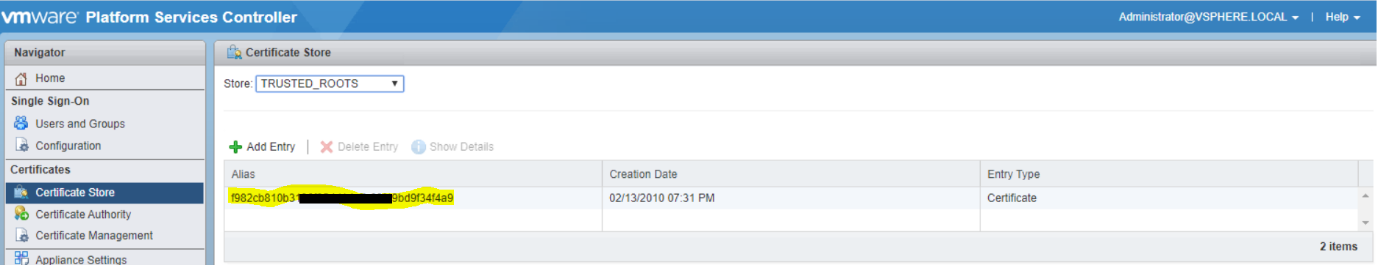
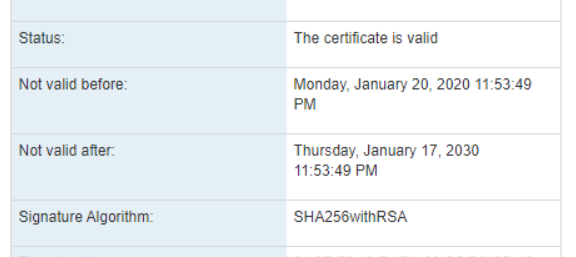
· Select Certificate and Click on Show Details. You can see that certificate is not valid.
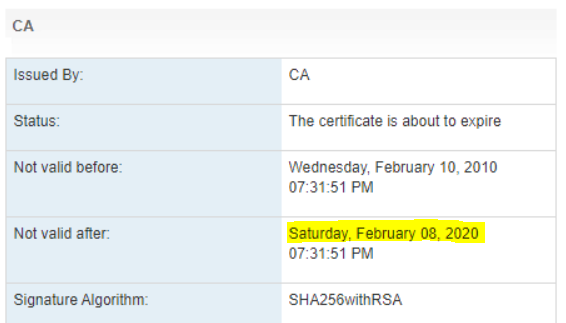
Now you might have question that if above certificate is valid till February 08, then why its showing error notification now (20th Jan – in our case)?
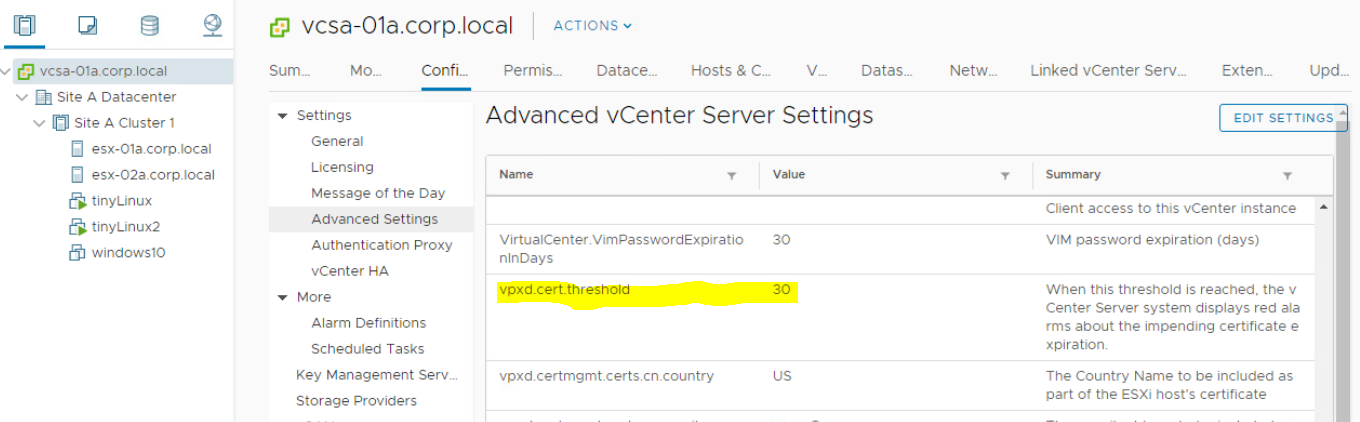
This is because of threshold value set for the notification. When this threshold is reached, the vCenter Server system displays red alarm about the certificates which is about to expire.
· Login to vCenter Server. Click on vCenter Server > Configure > Advanced Settings > Check value for vpxd.cert.threshold
· Open Putty and SSH to PSC server. Use root credentials to login.
login as: root
VMware vCenter Server Appliance 6.5.0.32000
Type: VMware Platform Services Controller
root@vi-psc-01's password:
Connected to service
* List APIs: "help api list"
* List Plugins: "help pi list"
* Launch BASH: "shell"
Command> shell
Shell access is granted to root
· Type below command to open certificate-manager for vCenter Server Appliance(VCSA)
o root@vi-psc-01 [ ~ ]# /usr/lib/vmware-vmca/bin/certificate-manager
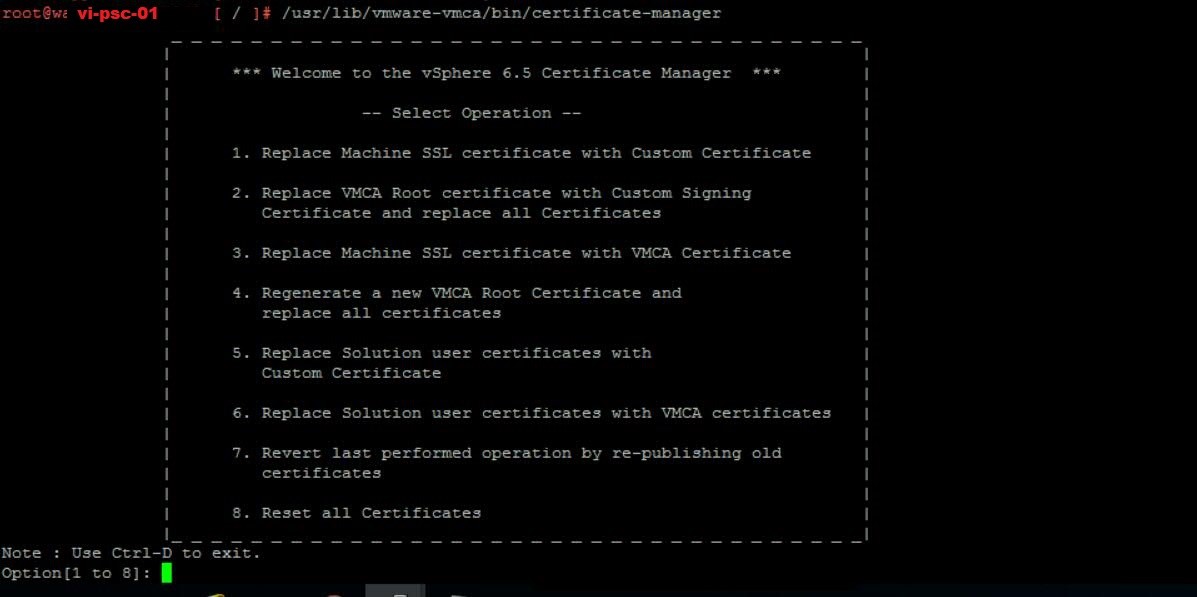
· Select Option 4 to regenerate a new VMCA Root Certificate and replace all certificates
o Option[1 to 8]: 4
o Do you wish to generate all certificates using configuration file : Option[Y/N] ? : Y
· Please provide valid SSO and VC priviledged user credential to perform certificate operations.
o Enter username [Administrator@vsphere.local]:administrator@vsphere.local
o Enter password:
· Please configure certool.cfg with proper values before proceeding to next step.
When ask for values, you can simply press ENTER key to leave default value for default Self-Signed certificate. However, if you want to use your own values, that’s your choice as per requirement.
o Press Enter key to skip optional parameters or use Default value.
o Enter proper value for 'Country' [Default value : US] : US
o Enter proper value for 'Name' [Default value : CA] : CA
o Enter proper value for 'Organization' [Default value : VMware] : VMware
o Enter proper value for 'OrgUnit' [Default value : VMware Engineering] : VMware Engineering
o Enter proper value for 'State' [Default value : California] : California
o Enter proper value for 'Locality' [Default value : Palo Alto] : Palo Alto
o Enter proper value for 'IPAddress' (Provide comma separated values for multiple IP addresses) [optional] : 127.0.0.1
o Enter proper value for 'Email' [Default value : email@acme.com] : email@acme.com
o Enter proper value for 'Hostname' (Provide comma separated values for multiple Hostname entries) [Enter valid Fully Qualified Domain Name(FQDN), For Example : example.domain.com] : vi-psc-01.vinsight.com
o Enter proper value for VMCA 'Name' : vi-psc-01.vinsight.com
· You are going to regenerate Root Certificate and all other certificates using VMCA
o Continue operation : Option[Y/N] ? : Y
· Stop vCenter services using below command.
o root@vi-psc-01 [ ~ ]# service-control --stop –all
· Start vCenter services using below command.
o root@vi-psc-01 [ ~ ]# service-control --start –all
· Login to PSC server using Web Client. (https://vi-psc-01/psc)
· Under Certificates tab, Click on Certificate Store > At right panel under, drop down Store > Select TRUSTED_ROOTS. All existing certificates will be in this list.
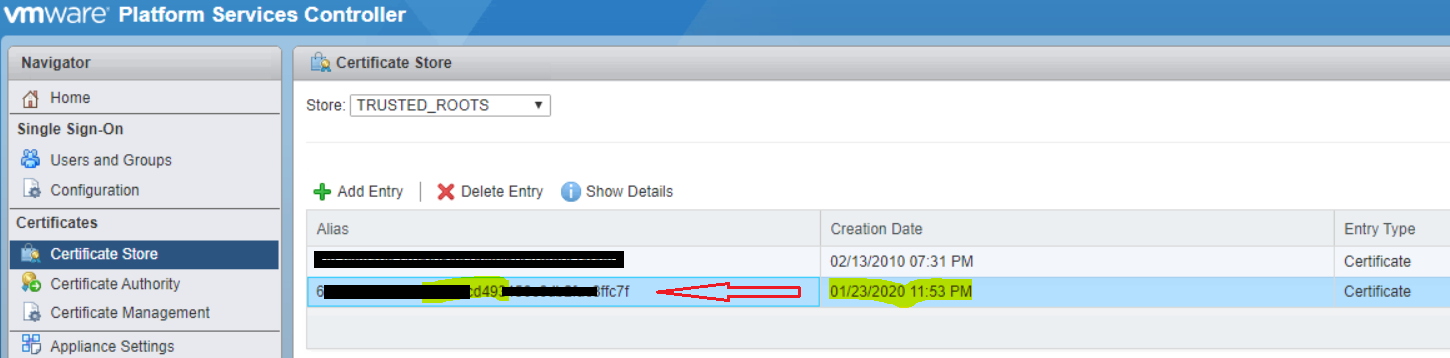
· Select Certificate and Click on Show Details. You can see that certificate is valid.
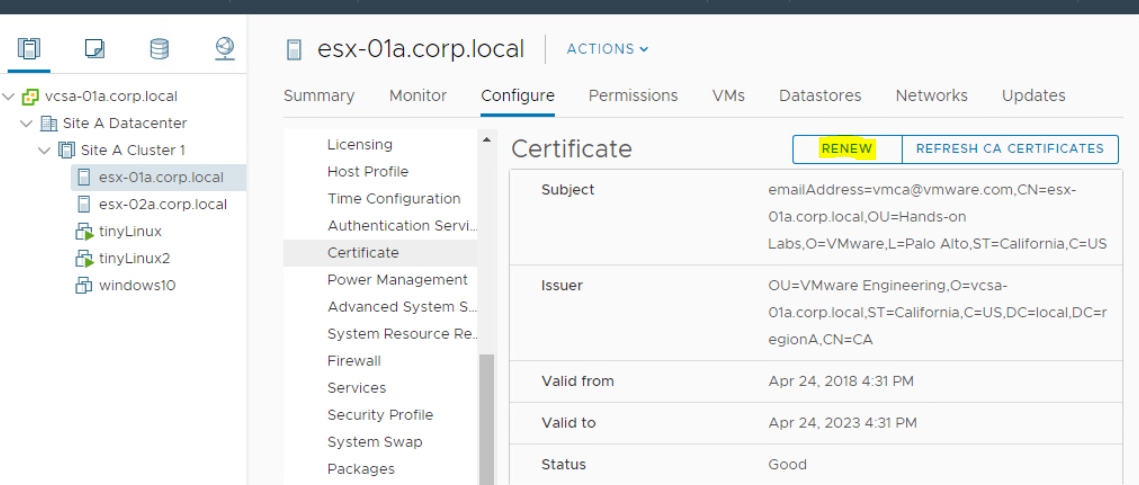
· Login to vCenter Server using Web Client.
· Click on each ESXi hosts > Configure > Certificate
· Click on Renew Option.